Every retailer knows the playbook: seasonal sales events are make-or-break. Whether it’s a July promo, back-to-school promotion, or the Black Friday weekend gauntlet, these events can bring in 30–40% of annual revenue.
Bots are planning for that rush too. They show up early, stay late, and wreak havoc across every layer of your stack. They impersonate customers, abuse promos, hoard inventory, and scrape your pricing data like it’s their job (because for some, it is).
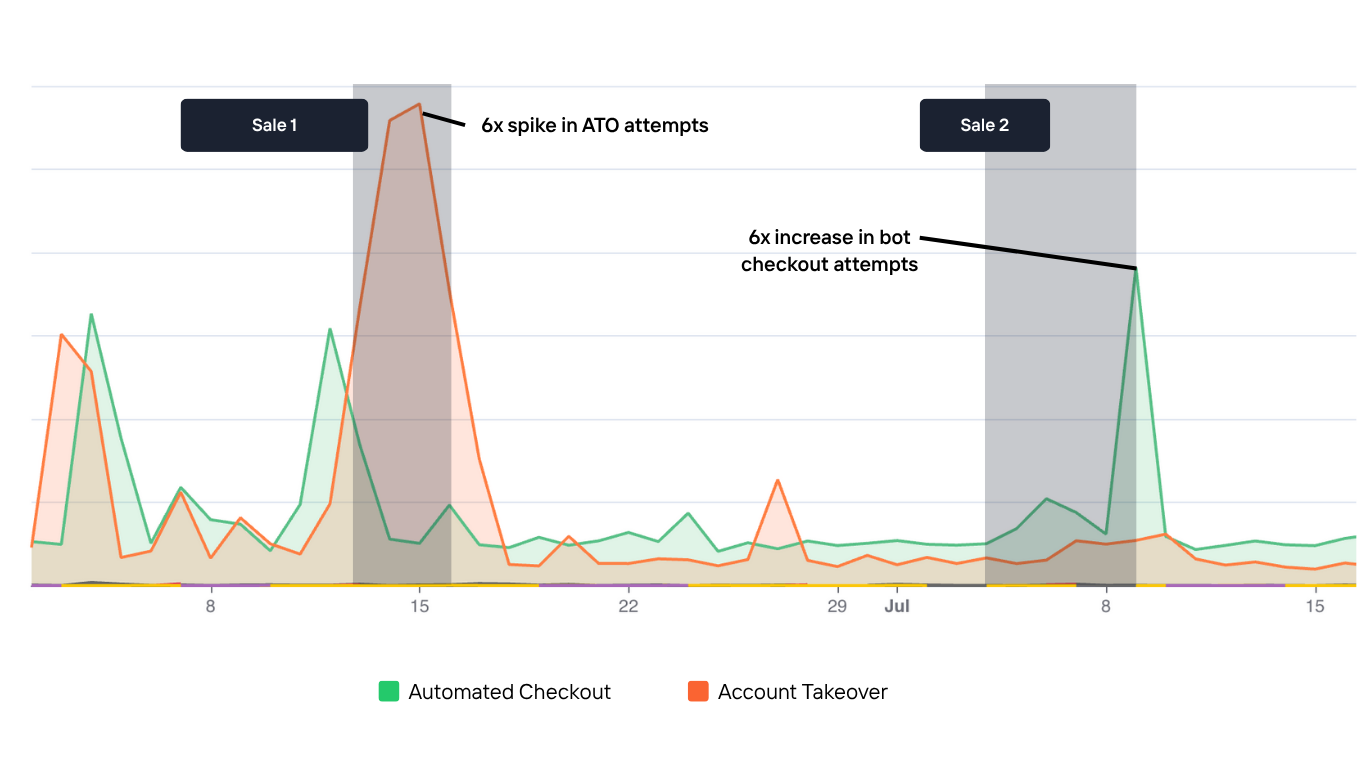
In fact, during one retailer’s Spring and July sales, Kasada observed a 6x spike in account takeover attempts and a 6x jump in automated checkout traffic. These weren’t random bursts, they were coordinated, high-volume attacks launched with precision timing.
Here’s what that looks like in real traffic:
That surge you see above? It wasn’t caused by script kiddies. These bots use sophisticated tools like CAPTCHA solvers, spoofed browsers, residential proxy networks, AI-generated identities, and well-maintained codebases. They blend in until your KPIs start hullicinating.
In this blog, we’ll break down the 5 most common (and costly) bot-driven threats we see hit retailers during seasonal sales – along with how Kasada detects and prevents them.
1. Fake Account Creation
Let’s start with one of the stealthiest threats: fake accounts. Fraud rings and discount hunters deploy bots to spin up thousands of accounts at once using throwaway emails, spoofed devices, and increasingly, AI-generated identities. They’re after anything with economic value: referral bonuses, new user discounts and signup bonuses, early access to limited drops. The worst part? Most traditional detection tools treat them like real users.
Signs of Fake Account Creation:
- A sudden spike in signups with similar email domains (e.g., maildrop or disposable providers).
- Unusual patterns in device types or user agents.
- New users failing to complete any meaningful actions post-signup.
- High volume of accounts tied to the same IP ranges.
The impact of fake accounts:
- Business: Service disruptions, polluted analytics, and inaccurate growth metrics due to inflated user numbers.
- Revenue: Increased costs from fraudulent transactions (e.g. chargebacks, lost inventory, account bans), wasted marketing spend, and promo abuse — all reducing ROI and margin.
- Brand: Customer frustration, negative social buzz, and potential legal exposure when fake activity goes unchecked.
Kasada stops these by inspecting the underlying automation patterns, not just user behavior, so you catch fraud before it hits downstream systems.
2. Credential Stuffing & Account Takeover (ATO)
Seasonal traffic spikes make your login pages ripe for abuse. Attackers use previously leaked credentials to test for reuse—before, during, and after major sales. These credential stuffing sessions often mimic legitimate users: clean headers, real browser signals, staggered timing. That’s exactly what makes them so difficult to detect.
During one retailer’s Father’s Day promotion, we saw a 6x increase in account takeover attempts. And at a major beauty retailer, Kasada observed a 118.6% spike in ATO activity immediately after their July sale which included 2.58 million credential stuffing requests in just 8 hours.
Without real-time bot detection, these attacks could have disrupted customers and led to widespread fraud.
What we’re seeing:
- Credential stuffing tools emulate real browsers and users.
- Attackers rotate IPs through residential proxies and mobile networks to stay below rate thresholds.
- Each username is tested only once, avoiding brute-force alerts that would typically detect conventional password-guessing attacks.
- Some bot operators abuse add-to-cart or checkout activity post-login to maximize their ROI.
Common signals to look for:
- Change in the average number of successful vs. unsuccessful login attempts.
- Spikes in login attempts from unusual geographies or unknown devices.
- Sessions trying to log in with more than 2 usernames.
Kasada identifies anomalies deep in the browser stack—signals most platforms overlook. And since we work in real time, you’re not left learning about a breach after the fact.
💡 Related Resource
Curious how ATO attacks are evolving across industries? Kasada’s Account Takeover Report breaks down the latest attacker techniques—and what leading brands are doing to stop them.
3. Promo Abuse
This one hurts the bottom line fast. Bots exploit promo codes, new user discounts, and referral programs—often working in concert with fake accounts to scale the damage. What looks like a successful campaign in your dashboard might actually be a fraud operation.
What we’re seeing:
- Coordinated bots cycle through fake accounts to farm promo codes.
- Some use automated scripts to test hundreds of discount codes in seconds.
- Others time abuse to hit just as sales launch, before real shoppers even log in.
Common signals to look for:
- Spike in redemptions from new accounts created within minutes.
- Decline in average order value during promos (due to stacked or misused discounts).
- High concentration of referrals from a single account.
Promo abuse often goes undetected until after a campaign ends, and by then, the damage is done. In one case, Kasada uncovered a vulnerability that allowed bots to redeem one-time promo codes across multiple devices simultaneously, resulting in unauthorized free meals. We blocked these attacks in real time and alerted the retailer to the underlying issue, helping them patch the exploit and protect future campaigns.
4. Cart Hoarding & Automated Checkout
This tactic manipulates both inventory and perception. Bots rapidly cart high-demand items to create artificial scarcity, preventing legitimate customers from checking out. In many cases, these bots go a step further—automated checkout tools complete the full purchase in seconds, locking real users out of the transaction entirely. Resellers and scalpers use this to grab limited-edition items or bulk-buy discounted inventory, then resell it at face value or higher for profit — all while disrupting retailers’ ability to serve real customers.
What we’re seeing:
- Resale bots use browser emulation to mimic VIP shoppers.
- Scripts instantly cart and checkout—often using saved credentials or gift cards.
- Automated checkout in combination with ATO, where accounts are tested for access leading up to a sale, so that compromised accounts can be used for speedy checkout at drop time.
- Attackers dry-run drop times and queue mechanics before the real sale.
Common signals to look for:
- Sudden inventory spikes in cart but not in completed transactions.
- High cart abandonment from real users shortly after the sales launch.
- Geographically dispersed checkouts using the same device fingerprint.
Kasada looks beyond surface-level requests. We analyze velocity, geography, and session behavior to determine carting intent and stop inventory hoarding in its tracks.
5. Scraping
Thanks to AI, bots are increasingly getting better at scraping pricing, availability, and product metadata to power competitive intelligence, phishing sites, or fake marketplaces. These scrapers often rotate through real browser instances, mimicking human behavior to get past detections.
What we’re seeing:
- Competitive pricing bots rotate through hundreds of residential IPs to evade rate limits.
- Scrapers adapt to JS rendering and headless detection with new open-source tools.
- Some use referer spoofing and hidden UTM tags to blend in with organic traffic.
- Freebie bots constantly scan inventory to identify price errors or steep discounts.
Common signals to look for:
- Traffic with high pageview-to-session ratios but no add-to-cart or conversions.
- Surge in API calls hitting product or price endpoints directly.
- High number of sessions with 1-3 second dwell times across many SKUs.
Our threat intel team monitors underground botting communities to stay ahead of these tools. Kasada blocks scraping attempts in real time without adding friction to genuine shoppers.
One Retailer’s Story: Spring Sale Defense in Action
In the weeks leading up to their April Spring Promo, a major beauty retailer faced a surge of bot-driven abuse. Credential stuffing attacks surged, reaching peaks of 450 login attempts per second, and ongoing vulnerability scans and API abuse strained their infrastructure. Despite using a legacy bot mitigation provider, the retailer was still seeing up to a million monthly password resets, polluted analytics, and growing team fatigue from server restarts and fraud triage.
When Kasada entered the picture, protection was deployed just in time for the promo window. Our system immediately began detecting and blocking bots that other tools missed, ensuring the success of their spring sale.
Key outcomes:
🔒 Bots blocked from login endpoints during the sale
💥 Password resets dropped from 100K–1M/month to just 100/month
🚫 Account takeovers were successfully prevented
📊 Analytics were preserved, giving clean visibility into shopper behavior
⚙️ No downtime or crashes—for the first time during a major sale
💬 Customers noticed, with social media praise for a smoother purchase experience
This wasn’t just a win for security—it was a win for marketing, customer loyalty, and operational sanity.
Protecting Sales Events with Kasada
We do bot mitigation differently. There are no CAPTCHAs, no clunky scoring engines, and no long tuning cycles. Our protection is easy to manage, invisible to humans, and infuriating to bots.
With Kasada, you get:
- Real-time detection and mitigation;
- Frictionless experiences for real users;
- Actionable insights for both technical and business teams.
If you’re planning a back-to-school promo, a Labor Day sale, or prepping for Q4’s holiday shopping season, let’s chat and help plan for success. We’ll show you what’s hitting your site now, what we expect for your upcoming sale, and how to stop the bots once and for all.
👉 Talk to an expert and Kasada in action.