ADVERSARIAL TECHNIQUES
The sneaky shift: Adversaries are simply bypassing defenses
In recent years, motivated actors have begun to directly target the products used to defend your apps and fool them into thinking attack traffic is from real users. The arms race is underway and traditional tools can’t keep up.
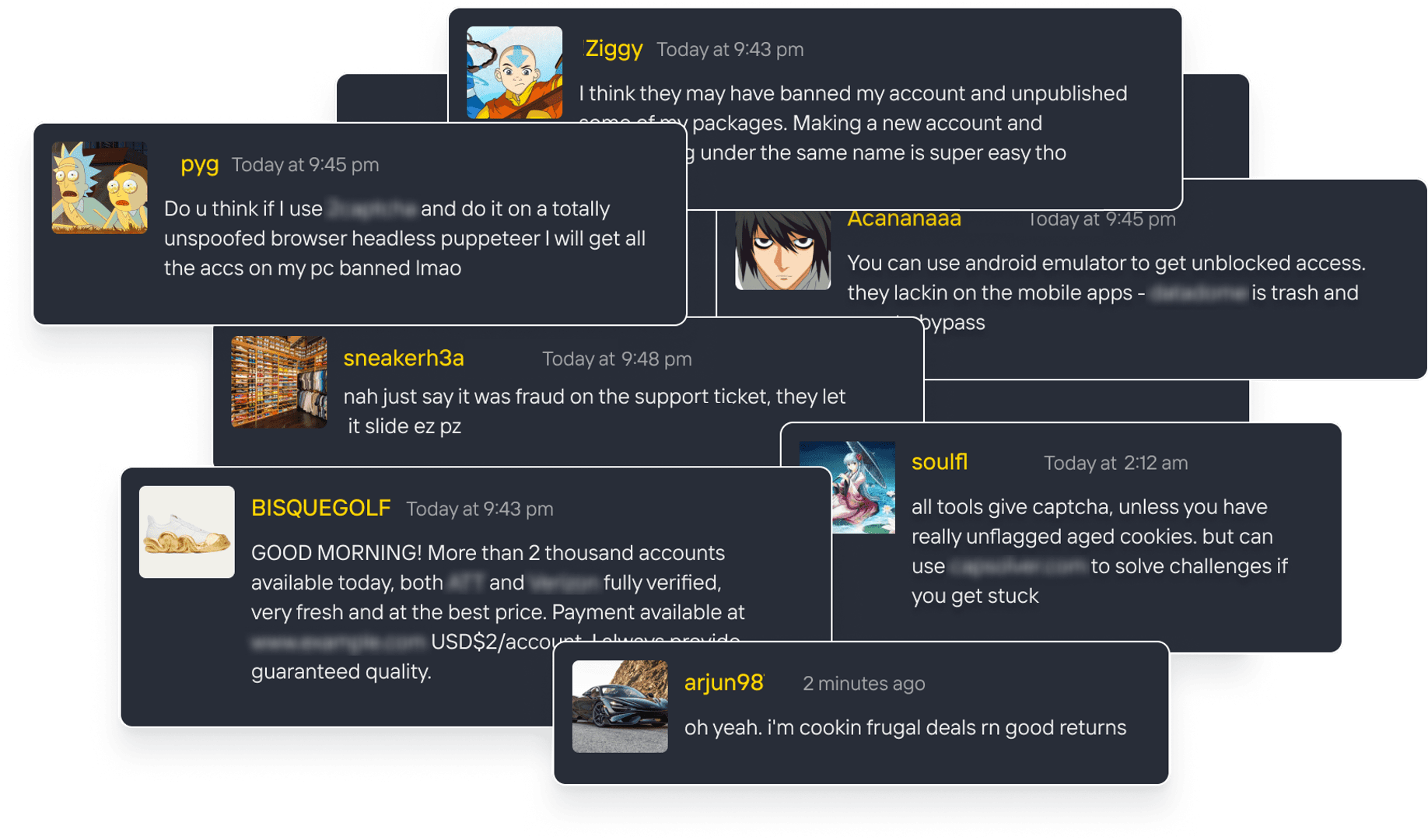
Attackers meet underground to make bots mimic humans
In financially motivated communities, adversaries share ideas, tools, and services that make bots look and act like real users. The result? A supply chain that helps threats evolve to quickly bypass defenses.
Cheap. Accessible. Effective. Attackers have a lot of tricks. To bypass defenses and evade detection, adversaries employ an array of techniques that defeats traditional bot management tools. Easy to find. Easy to use. Hard to defeat — with outdated “solutions.”
Cheap. Accessible. Effective. Attackers have a lot of tricks.
To bypass defenses and evade detection, adversaries employ an array of techniques that defeats traditional bot management tools. Easy to find. Easy to use. Hard to defeat — with outdated “solutions.”
Solver services
Some threat actors have realized the real business is in attacking the bot management solutions, not your applications directly. Like a SaaS vendor, they build and sell “solver services” that help fellow adversaries appear human and easily bypass bot defenses. This means there are quickly accessible bypasses for most bot management vendors — you can even find them using Google!


Solver services
Some threat actors have realized the real business is in attacking the bot management solutions, not your applications directly. Like a SaaS vendor, they build and sell “solver services” that help fellow adversaries appear human and easily bypass bot defenses. This means there are quickly accessible bypasses for most bot management vendors — you can even find them using Google!
SOPHISTICATION TO USE:
COST:
80¢ – $3.50 per 1,000 solves
- 1An attacker sets up a solver service for a specific bot management defense.
- 2Other, less resourceful attackers exchange money for human bypass tokens
- 3Bot traffic disguised as human traffic bypasses anti-bot defense

Headless browsers and device simulators
Basic detections of the client environment are no longer effective. Attackers use highly customized versions of open-source DevTools like Puppeteer (with the Extra Stealth plugin) to appear as a legitimate client.
- 1Attacker uses fully automated environments with human-like behavior to bypass defenses
SOPHISTICATION TO USE:
COST:
$20-$500
per month depending on scale
SOPHISTICATION TO USE:
COST:
$20-$500
per month depending on scale
- 1Attacker uses fully automated environments with human-like behavior to bypass defenses
Residential proxy networks
Traditional detections like IP reputation and IP-based rate limiting are no longer effective, thanks to services that cheaply allow attackers to proxy their traffic through millions of legitimate consumer IP addresses. Free VPNs often secretly act as exit nodes on unsuspecting real users, providing cover for attackers.


Residential proxy networks
Traditional detections like IP reputation and IP-based rate limiting are no longer effective, thanks to services that cheaply allow attackers to proxy their traffic through millions of legitimate consumer IP addresses. Free VPNs often secretly act as exit nodes on unsuspecting real users, providing cover for attackers.
SOPHISTICATION TO USE:
COST:
$50-500 per month
- 1Attacker subscribes to a residential proxy network service
- 2IP-based defenses bypassed by hiding in legitimate IPs from all over the world

CAPTCHA bypasses
CAPTCHAs are ineffective and frustrate users. Attackers cheaply bypass them by using a combination of AI/ML, human farms, and reverse engineering — services that are, once again, easily findable through Google. The only things that benefit from CAPTCHAs are the bots who now appear human, thanks to “successful solves.”
- 1Attacker extracts unsolved CAPTCHA from the anti-bot solution
- 2Attacker pays CAPTCHA bypass service to solve the CAPTCHA
- 3Bot bypasses anti-bot defenses with solved CAPTCHA
SOPHISTICATION TO USE:
COST:
50¢ per 1,000 CAPTCHAs
SOPHISTICATION TO USE:
COST:
50¢ per 1,000 CAPTCHAs
- 1Attacker extracts unsolved CAPTCHA from the anti-bot solution
- 2Attacker pays CAPTCHA bypass service to solve the CAPTCHA
- 3Bot bypasses anti-bot defenses with solved CAPTCHA

Machine learning poisoning
Machine learning-based detection can sound promising, but often doesn’t hold up against adversaries that know how to fool it. By customizing their tooling, attackers can feed ML-based detections statistically accurate (but fake) data, which appears human.
Machine learning poisoning
Machine learning-based detection can sound promising, but often doesn’t hold up against adversaries that know how to fool it. By customizing their tooling, attackers can feed ML-based detections statistically accurate (but fake) data, which appears human.

SOPHISTICATION TO USE:
COST:
FREE (essentially)
- 1Bot confuses the machine learning model by overloading it with fake information
- 2
Machine learning defenses are bypassed by hiding amongst the noise

De-obfuscation
Bot Management often uses obfuscated code to hide how bot detection works. Most solutions rely on open-source tools with well-known vulnerabilities to de-obfuscation. Once an attacker understands exactly how your defenses work, they are effectively useless.
- 1
Attacker obtains detection script
- 2Attacker reverse engineers script and learns the data needed to classify as human
- 3
Bot bypasses the anti-bot solution by providing it with fake data
SOPHISTICATION TO USE:
COST:
Free (essentially)
SOPHISTICATION TO USE:
COST:
Free (essentially)
- 1
Attacker obtains detection script
- 2Attacker reverse engineers script and learns the data needed to classify as human
- 3
Bot bypasses the anti-bot solution by providing it with fake data
Want to learn more? Let’s learn together.
The Truth About Your Bot Detection’s Threat Intelligence
The traditional data used to differentiate between humans and bots can no longer be trusted. Bots are evolving quickly.
Freebie Bots: The Latest Threat to Retailers
Steep discounts drove Cyber Monday online sales to hit record highs, but some discounts were created by mistake.