SEE THE TRENDS
Key Findings
SEE THE TRENDS
Key Findings
361 Config Files
In Q1 2025, KasadaIQ observed 361 OpenBullet configs listed by adversaries.
1,000+ Brands
Over 1,000 large companies were targeted since January 2024, compromising millions of customer accounts.
2.5 Million Accounts Breached
Stock of stolen accounts peaked in early January, with nearly 2.5 million available for sale.
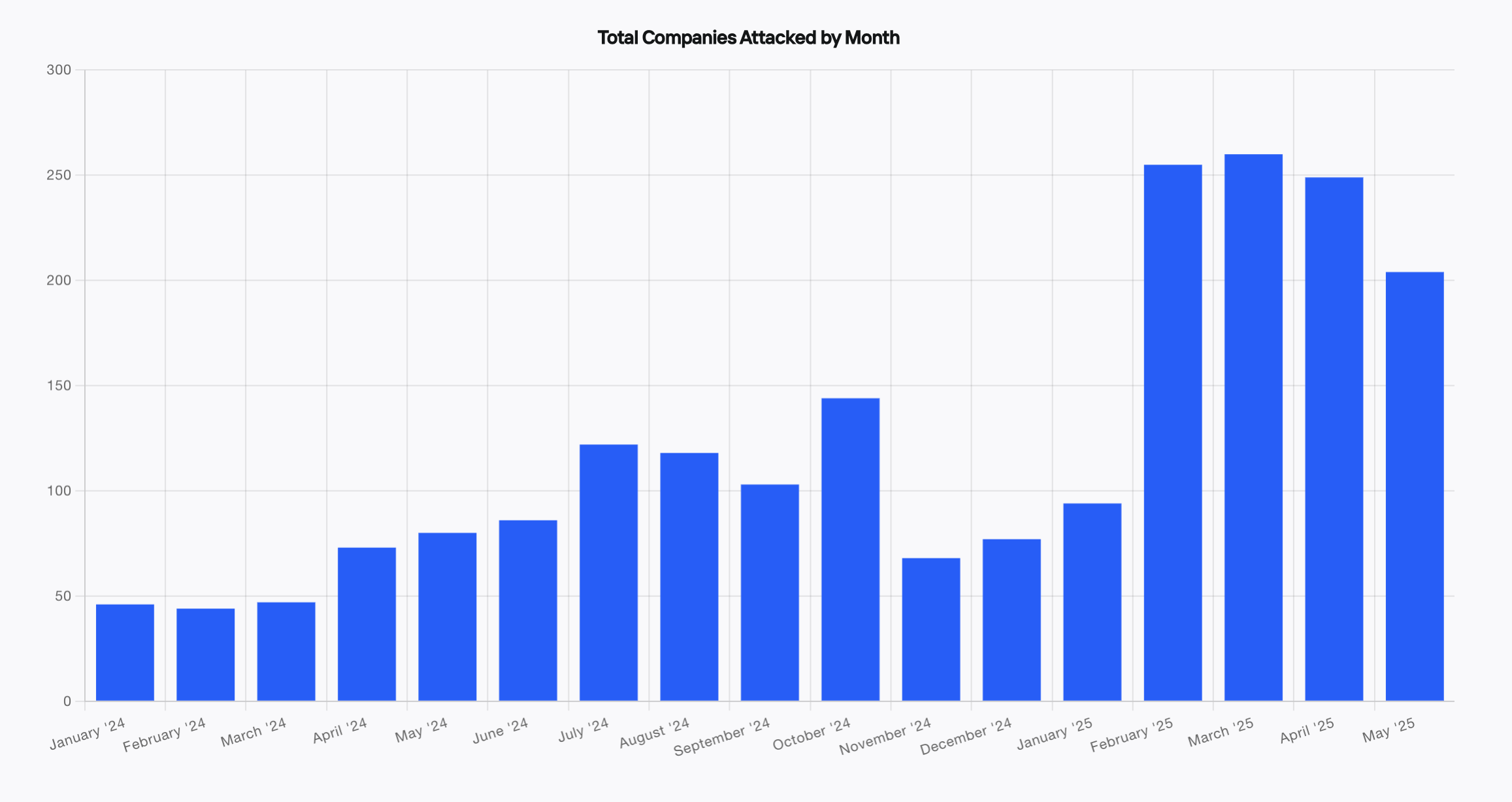
Tracking ATO: Monthly Attack Patterns
Kasada observed steady growth in ATO and fraud activity throughout 2024, with sharp spikes in October and again in early 2025. The surge coincided with enhanced monitoring of criminal marketplaces and culminated in a record number of stolen account listings in January—nearly 2.5 million. In Q1 2025 alone, 67% of all tracked account sales targeted webmail, retail, and social platforms. One group, ALTSRUS, stood out for its widespread ATO campaigns targeting vulnerable communities, including EBT-linked accounts, highlighting a troubling shift toward exploiting vulnerable communities..
👉 Explore the Q1 Threat Report to learn more.
Total Companies Attacked by Month
361 Config Files
In Q1 2025, KasadaIQ observed 361 OpenBullet configs listed by adversaries.
1,000+ Brands Targeted
Over 1,000 large companies were targeted since January 2024, compromising millions of customer accounts.
2.5 Million Accounts Stolen
Stock of stolen accounts peaked in early January, with nearly 2.5 million available for sale.
Tracking ATO:
Monthly Attack Patterns
Kasada observed ATO attacks spiking in summer months and October, highlighting the seasonality of bot-driven threats. These fluctuations may be driven by attackers with more free time in the summer — such as students experimenting with credential stuffing — and increased fraud activity in October as cybercriminals ramp up for the holiday shopping season, testing stolen credentials and refining their tactics before peak retail periods.
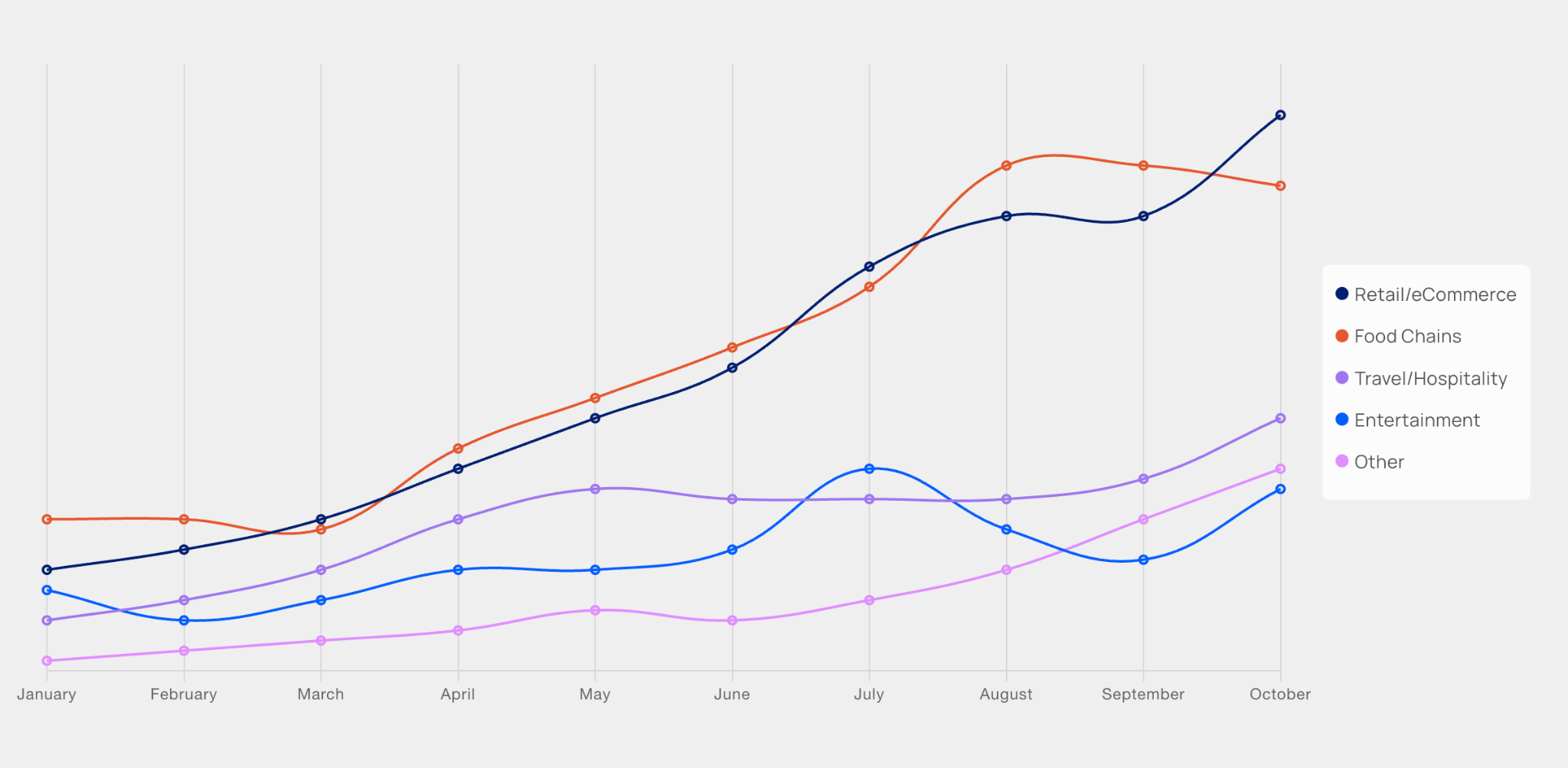
Industry Breakdown: Who’s Being Targeted?
Credential stuffing is a cross-industry threat, but certain sectors are more frequently targeted due to the high value of customer accounts, such as loyalty and rewards points, and the sensitive financial information and personal data they store.
Unique Companies Targeted by ATO Attacks (2024–2025), by Industry
Industry Breakdown:
Who’s Being Targeted?
Who’s Being Targeted?
Credential stuffing is a cross-industry threat, but certain sectors are more frequently targeted due to the high value of customer accounts, such as loyalty and rewards points, and the sensitive financial information and personal data they store.
Traditional Defenses Are Failing
Among targeted and compromised companies, 85% already had a bot detection solution—proving just how aggressive and advanced these attackers have become.
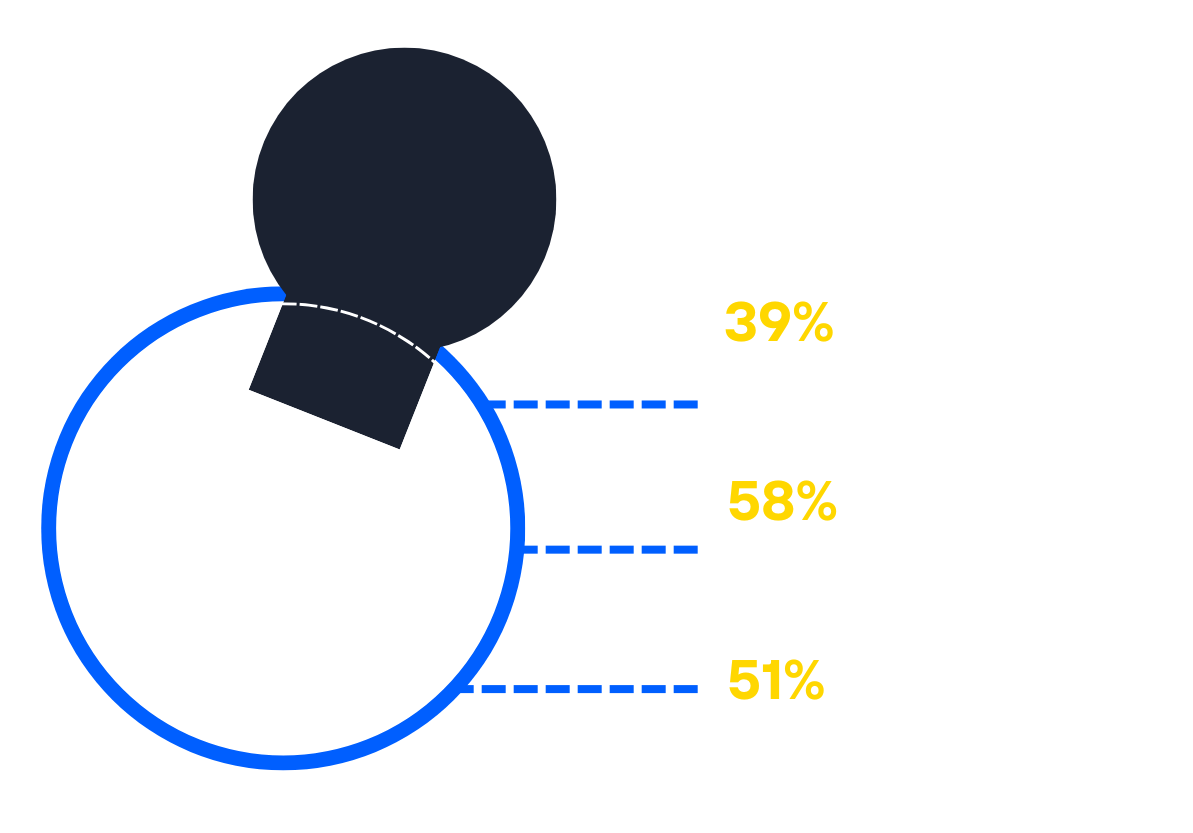
Traditional Defenses Are Failing
Among targeted and compromised companies, 85% already had a bot detection solution—proving just how aggressive and advanced these attackers have become.

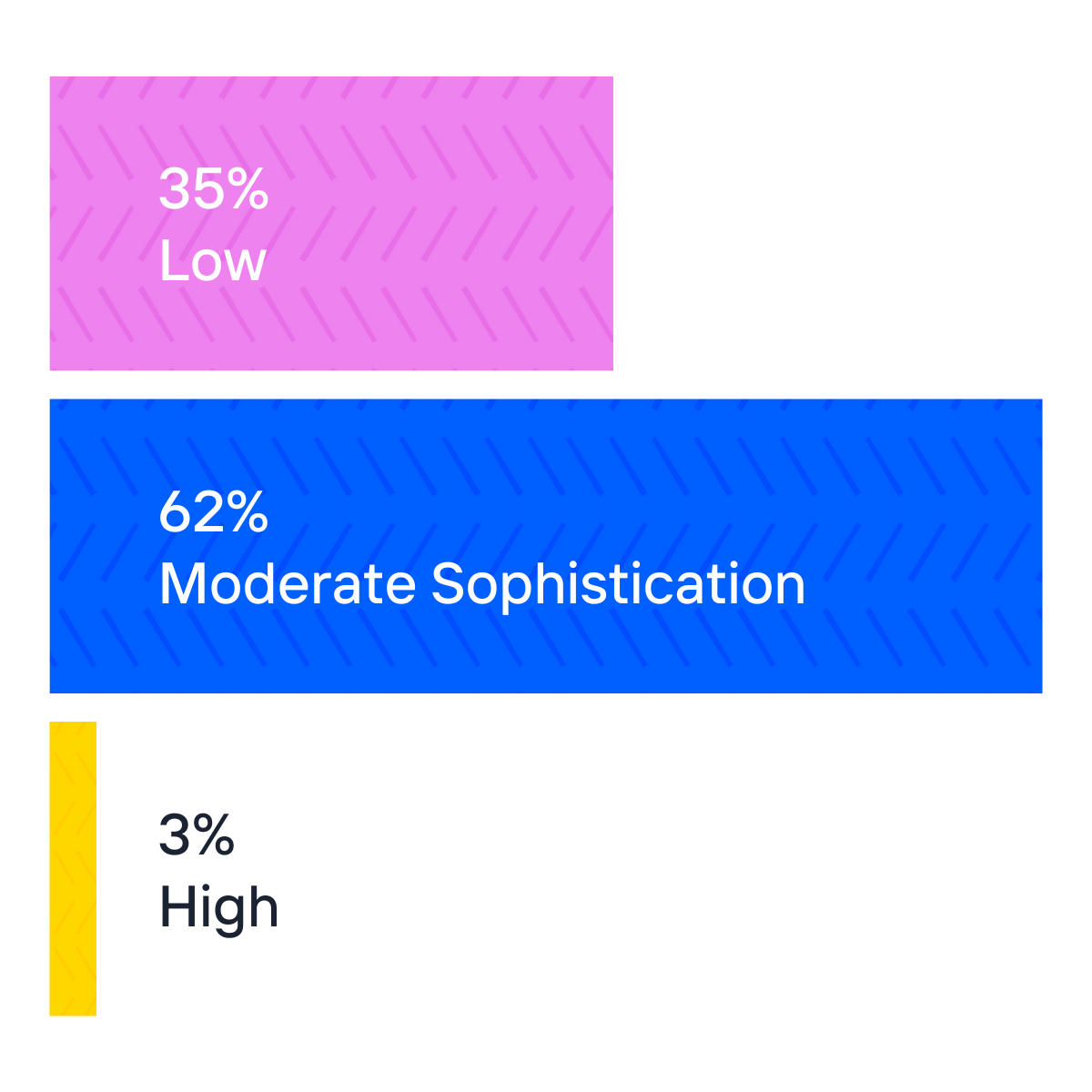
How Bots Are Outsmarting Detection
When launching account takeover attacks, threat actors use advanced tools like OpenBullet, which enable large-scale automation with minimal effort. This allows adversaries to configure custom scripts that bypass common defenses, such as CAPTCHA, using techniques like rotating proxies and mimicking human behavior to remain undetected.
How Bots Are Outsmarting Detection
When launching account takeover attacks, threat actors use advanced tools like OpenBullet, which enable large-scale automation with minimal effort. This allows adversaries to configure custom scripts that bypass common defenses, such as CAPTCHA, using techniques like rotating proxies and mimicking human behavior to remain undetected.

SEE THE TRENDS
Uncover how attackers exploit ATO—and how to stop them.
SEE THE TRENDS
Uncover how attackers exploit ATO—
and how to stop them.
The latest from Kasada
AI agent trust: What to allow, what to block, and what to prepare for
As AI agents blur the line between real customers and automated abuse, this live session with Kasada's Head of Product breaks down how teams manage agent trust across discovery, accounts, and checkout—without sacrificing revenue or security.