The Buy Now Pay Later (BNPL) industry is still relatively new, but accounted for 2.1% of all global e-commerce transactions in 2021 (nearly $97 billion) and is expected to double by 2024, according to CNBC.
This presents new opportunities for retailers — offering the latest payment methods like BNPL as a means to acquire new customers, increase order size, and boost conversion rates by 20-30%.
As their popularity grows amongst consumers and retailers for their convenience and accessibility, they’re also catching the eye of bot operators looking to exploit the market.
Aware of the influx of non-human traffic via bots, many BNPL organizations have implemented various verification and security measures throughout the digital payment journey (enrollment, login, shopping, payment, etc.) to stop them. Unfortunately, an unintended side effect has been additional friction to the checkout process.
Why are fraudsters targeting BNPL companies?
Simply put, it’s lucrative, and cybercriminals follow the money. Similar to carding, credit card and gift card fraud, BNPL fraud is another avenue to make a profit and stick someone else with the bill. It also allows cybercriminals a way to attack both consumers and merchants, leaving the BNPL provider and the banks who back them responsible for payment fraud.
While consumer fraud is more common, merchant fraud is more malicious, giving fake merchants a method to ‘wash’ fraudulent funds for money laundering activities. With these new attack vectors and vulnerabilities fraudsters are seeking to exploit, the greater the risk of fraud.
How are bots used to abuse logins?
Bot operators most commonly exploit the login of FinTech organizations. This can be an easy gateway to create new customer and merchant accounts or take over existing ones using a method called credential stuffing. Fraudsters either rent bots created by their peers who have worked to bypass many well-known bot defenses or create their own using insight from forums and online communities in order to carry out attacks.
Fake Account Creation
Automation allows fraudsters to create new consumer and merchant accounts quickly and easily. Using databases of stolen identities purchased on the dark web for consumers and fake or stolen business credentials for merchants, bot operators consistently try to create thousands of accounts a day. One BNPL provider that Kasada now protects previously experienced almost 170,000 fake account creation attempts per week that were getting through their legacy bot solution provider.
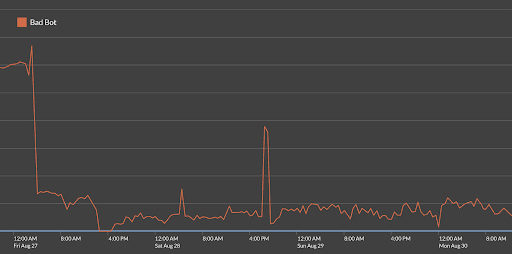
Figure 1: Before implementing Kasada, a BNPL provider experienced a constant stream of 10,000 automated fake account creation attempts each day, which increased to over 120,000 attempts during the weekend.
While most attempts to create fake accounts are unsuccessful, a small percentage of them can pass verification checks.
For fake consumer accounts, they are monetized by immediately making purchases (buy now) and then refusing to pay the installments (pay never). Alternatively, some fraudsters choose to sell the account on the dark web for the highest bid.
A recent victim of a consumer attack, columnist Karen Maley, shared in the Financial Review how her driver’s license information was fraudulently obtained and used to open various BNPL accounts in her name on sites like humm, Openpay, and LatitudePay. Unfortunately, these attacks aren’t uncommon and are an increasing concern for many emerging FinTech organizations.
New fake merchant accounts lure unsuspecting customers to purchase goods from their store that either don’t exist or they have no intention of fulfilling. In this scenario and others like it, the merchant is immediately paid in full by the BNPL organization. After the BNPL provider realizes fraud has occurred, they attempt to recover the funds, but by then it is too late and the money is gone.
In both instances, fraudsters wreak havoc on back-end fraud teams as their machine learning, data science, and intelligence algorithms can’t catch everything. Even with robust payment authentications and anti-fraud solutions, 5% of all digital payment fraud still slips through the cracks, according to an article by About Fraud.
Account Takeover (ATO)
Another common target for fraudsters is to take over established consumer accounts to leverage earned credit and make purchases without the intention of making payments. Through the use of automation, bots test the login credentials that are reused across other websites in hopes that they’ll work. From there, an attacker can lock a person out of their own account, max out their credit limit, and leave individuals with debts they can’t pay. They can additionally make purchases to fraudulent BNPL merchants as a way to send legitimate funds to illegitimate businesses.
The number of fraudulent login attempts increased by a massive 282% last year according to a report published on GlobeNewswire. A common source for these login credentials comes from data breaches, phishing attacks, or API vulnerabilities. According to the Identity Theft Resource Center’s 2021 Data Breach Report, there were 1,862 data breaches in 2021, a new record high. With more attacks and breaches occurring every year, it’s imperative BNPL providers can protect users from credential stuffing.
What Can Be Done to Fight BNPL Fraud?
BNPL organizations should use a multi-layered approach to risk management and fraud protection. A good first layer of defense will help prevent fake account generation and ATO schemes and significantly reduce the strain and burden of downstream security. With fewer malicious requests getting in, fraud and security teams can breathe easier and refocus their attention and efforts on other high-impact areas.
With a majority of online fraud initiating at the login, Kasada recommends the following to bolster security, first at the login, and then expanding from there:
- Implement the use of an anti-bot solution as the first layer of defense. This eliminates automation from getting into your system and carrying out various attacks.
- Add a second layer of security by enabling Multi-Factor Authentication (MFA) or One Time Passwords (OTPs).
Solutions often work better when layered together, but companies should always keep in mind the impact their solutions have on end-users. Enabling MFA or OTP requires users to adopt new technology, and CAPTCHAs often frustrate customers instead of fraudsters.
Unfortunate Tradeoff – Protection vs. Friction
When attempting to strengthen login defenses, many organizations are adding additional friction to the customer experience. Ultimately, this is a difficult tradeoff as introducing friction reduces conversions, and to be a viable solution for both retailers and providers, offering alternative payment methods must show an uptick in conversions.
Making matters worse, adversaries have learned to work around such defenses. CAPTCHAs have become easily bypassed with various technologies and services like CAPTCHA farms to help attackers solve challenges. Bot operators have also figured out ways to trick MFA/OTPs. Otp[.]agency was a web-based bot service designed to intercept OTPs. With the target’s login credentials already known, the bot service automated phone calls and messages and convinced the target to repeat their one-time password for “authentication purposes,” according to KrebsonSecurity.
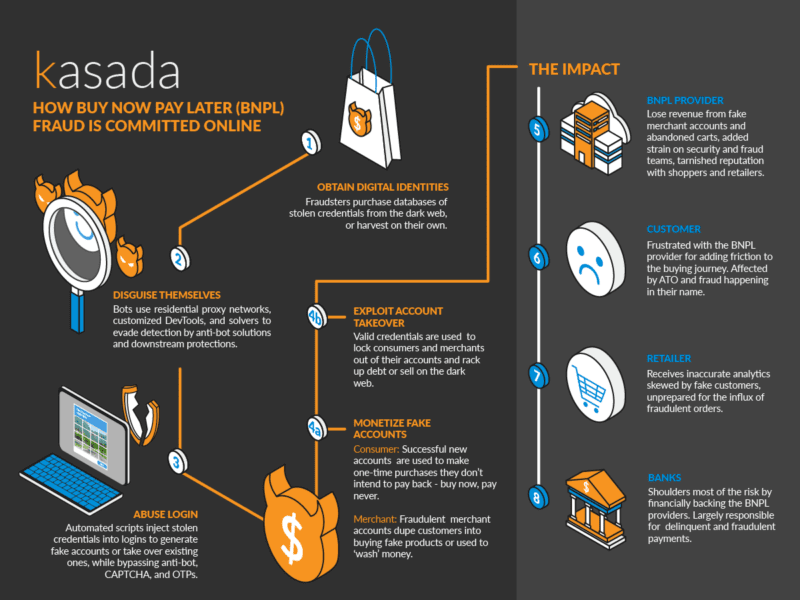
Figure 2: How Buy Now Pay Later (BNPL) Fraud is Committed Online
Not being able to seamlessly protect against attacks at the login can lead to:
- Customer and merchant account takeovers and fake account generation
- Poor customer and merchant experiences with fewer conversions
- A tarnished brand reputation that consumers, retailers, and banks won’t trust
- Surging infrastructure costs from high bot traffic
- A strained fraud team with a higher risk of lost revenue
Breaking the Tradeoff Between Protection & Friction
When weighing the tradeoffs above, many BNPL providers understandably chose aggressive protection over a frictionless buying journey as the risk of payment fraud is too high. However, customer voices are becoming louder and calling for a better experience. In a press release, Nir Aravot, Product Manager of Customer Authentication Platform for Klarna, a popular BNPL provider, stated “security is not an excuse for a poor experience, and we know that customers will simply not accept it.” Fortunately, there are solutions out there that don’t compromise a great user experience for security.
Securing Logins from Abuse, without a CAPTCHA
Kasada set out to develop a better way of protecting logins from malicious automation. One that doesn’t have to first let requests in before stopping them, and one that doesn’t require the use of CAPTCHAs. By doing so, BNPLs and retailers can reap the benefits of the payment method while reducing friction and minimizing the downstream cost and complexity of fraud.
Kasada identifies the presence of automation using a zero-trust philosophy that assumes all requests are malicious, allowing us to stop zero-day threats and new bots never seen before. These defenses are invisible and verify online users with precision, removing the need for CAPTCHAs or complex scoring rules. To deter and frustrate fraudsters, Kasada fights back by making it too computationally expensive to conduct automated attacks.
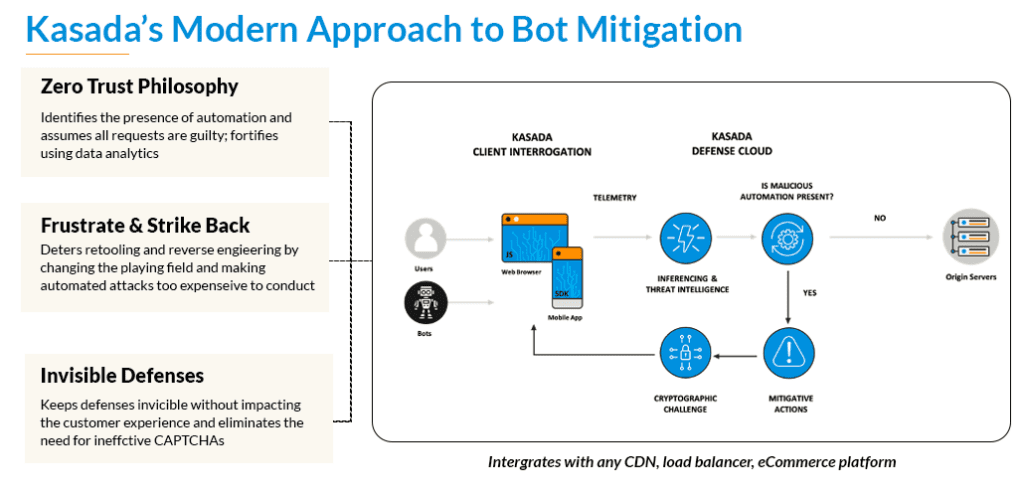
In contrast, legacy detection systems let automated requests enter their infrastructure in order to look for suspicious activity that flies under the radar until it is too late. With over 45 million users and counting, BNPL providers can’t afford to allow these requests in on the first request as it poses too much of a risk.
Summary
The Buy Now Pay Later industry shows much promise and no signs of slowing down any time soon. BNPL is designed to make online shopping more accessible and convenient to people around the globe while improving conversion rates for retailers. The popularity of these new forms of payments, however, is quickly attracting the attention of cybercriminals and fraudsters looking for new ways to exploit logins and commit payment fraud.
While there are many means of online fraud, automated exploits offer fraudsters a quick and easy way to create fake customer and merchant accounts and steal existing ones. In order for BNPL providers to thrive, they require modern bot detection that doesn’t frustrate users or compromise on security.
Kasada protects more than $20 billion in eCommerce payments annually and over a billion account logins. Request a demo to see how Kasada works or run an instant test to see if your website can detect modern bots from login abuse.





