The Driving Force Behind Creating KasadaIQ
At Kasada, we are all about stopping bots. We search through hundreds of millions of data points daily to understand, identify, and block automated threats for our customers. These data points are the digital fingerprints left each time a user interacts with or touches our customers’ infrastructure. It is easy to forget – as the daily count edges ever closer to a billion requests – that there is a human behind each of them, even the automated requests. A bot does not appear in the wild without human involvement. We must understand the humans behind these bots, their motivations, and their communities to predict their next move.
We started with an idea.
Imagine if we could detect attacks on companies that Kasada is not protecting. This idea of maximizing the positive impact Kasada delivers to the world captured our imagination, so we built a system to shine a light into these dark spaces.
We looked around and found no obvious solution; the established threat intelligence industry does not focus on business logic attacks. The Blade Framework, the bot equivalent to the Mitre ATT&CK Framework, categorizes everything neatly – but is not actionable. We knew that our service needed to move “beyond the browser” to detect bot attacks. It needed to know exactly who was being attacked. It needed to discover who was conducting the attack. And it needed to understand the magnitude and impact of the attack.
We needed a system that enabled us to predict the likelihood that a company was – or was about to be – attacked.
We designed KasadaIQ to be that system, consuming millions of signals to help Kasada understand the shape of the botting ecosystems. These signals, taken from all corners of the Internet, provide high-fidelity data that enables Kasada to proactively protect customers of our IQ service. Intelligence, in any form, is of no value unless it can be consumed and actioned by the recipient – in our case, our customers.
In the early stages of Kasada’s Threat Intelligence team, we provided intelligence to our existing customers – helping them to uncover insider threats, configuration issues being exploited by fraud groups to conduct large-scale account enumeration and reverse engineering bot software to enhance customer defenses. As our team grew in size and coverage, we expanded our defense capability to monitor other fraudulent activities affecting our customers. What we uncovered was a huge ecosystem of activity consisting of highly financially motivated individuals. Bot developers, shipping agents, stolen account providers, covert infrastructure, and solver services providing bypasses for anti-bot technologies all exist in this criminal ecosystem, trading on reputation and in stolen goods.
KasadaIQ exists to augment a traditional threat intelligence capability which is focused on ingesting IP addresses, file hashes, and providing signal to a security operations center (SOC). We do things differently by uncovering campaigns focused on an organization’s business logic. We identify when a threat actor is building or has built a capability to exploit a logic flaw, whether that is on a login endpoint, through the construction of a refund loop, or through stacking reward points to gain an advantage over a system. Each alert from our extensive collection is triaged by one of our analysts, who ensures that any alert or intelligence an organization receives is high quality and actionable. We do not only rely on automated collection; each week, one of our analysts conducts manual collection for each organization, identifying information in other locations not currently captured by our collection. We understand that cybersecurity is a non-static problem, and we need to be in the communities in which our adversaries operate. When they move, we move.
Delivering actionable intelligence is core to KasadaIQ and ensures our customers can reduce their response times when an alert is generated. We realized that our unique presence in the bot communities lets us help our customers see data they have no way of seeing today.
Now, let’s see how this all comes together in a real-life example.
In September 2023, a criminal group released a capability to bypass the protections of a large global retailer to conduct a credential stuffing campaign. After 14 days of the release, we found the first public proof of success published in a different forum. We saw that the success of this capability was limited. Another bot author released a new capability the next day, which improved and built on the previous capability. Within 24 hours, accounts for this global retailer were available on a criminal marketplace, with Kasada identifying customers of this company complaining of account takeovers on social media. Within a day of the first accounts appearing on the marketplace, the number of accounts for sale peaked, and within four days, three additional sellers had accounts from this company for sale.
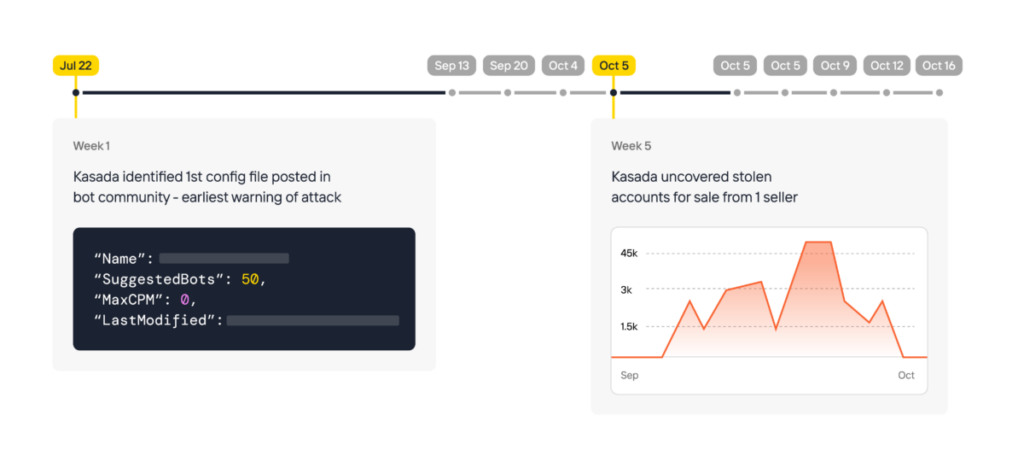
Figure 1: Example of a real-life account takeover timeline, based on the information KasadaIQ can gather, analyze, and report on for customers.
With KasadaIQ for Fraud, this organization would have received an alert when the capability was first released. Credential stuffing and account takeover attacks can snowball very quickly, leading to loss of revenue and damage to brand reputation. Knowing when a threat actor is building a capability and inspecting that capability provides an organization time, which is a huge advantage in any cybersecurity scenario.
In Splunk’s 2023 State of Security report, they identify that the mean time to detect a threat is 2.24 months or 9 weeks. KasadaIQ gives you an advantage over these sophisticated threat actors and significantly reduces the mean time to detection.
It’s not every day you can create a service that will have such a profound impact. We are proud that KasadaIQ will help more and more brands protect their customers and their businesses against evolving, advanced fraud.
Get your free, personalized KasadaIQ snapshot here. If you’re interested in chatting about the service, you can get in touch with us here.




