Today, Kasada unleashed the latest evolution of its bot defense platform. Essential with this launch is always evolving protection and securing the authenticity of web traffic data by forcing attackers to run their code in real time, in Kasada’s environment. A primary reason for this is legacy defenses are easily tricked by bots using fake data to to masquerade as legitimate human users.
What does Ocean’s 11 have to do with defending against online attacks?
There’s a famous scene in the 2001 heist film “Ocean’s 11” when the casino manager Terry Benedict (Andy Garcia) realizes he’s being robbed. It’s a busy night in Las Vegas, and the security team is monitoring the casino vault’s video feed. Everything appears normal… then Benedict’s phone rings. The casino’s vault is being emptied at that very moment. How? Danny Ocean’s crew (George Clooney) is feeding fake video footage to the security room. As proof, the monitors flicker briefly with the real footage – two bound guards and robbers with bags of money.
The scenario depicted in “Ocean’s 11” is not a Hollywood fantasy but a daily reality in the world of cybersecurity. Online attackers, akin to Danny Ocean’s crew, manipulate signals to deceive security systems, infiltrating networks and compromising data.
Falsifying Data to Trick Anti-Bot Detection
Today’s blog highlights the shocking ease with which bad actors can bypass cybersecurity defenses by sending false signals, rendering even the most sophisticated detections useless.
Kasada works with the world’s biggest retail, hospitality, and eCommerce brands. And we are continuously surprised that most are unaware of their legacy bot defense solution’s fatal flaw: It’s easily tricked by adversaries who falsify data to fool the system. No matter how sophisticated, the security detections will be bypassed and exploited if the data collected is faked – and the system can’t tell. A pretty traffic dashboard that shows no problems is that fake casino video feed; strip it away, and the humans are actually bots in disguise.
They unlock the whole vault and steal the cash.
A Real-World Example
Here’s a typical example capturing the moment Kasada began protecting website traffic for a large North American enterprise. This customer was already using a leading CDN’s premier bot detection service, and Kasada detections were deployed “behind” it. The bad bots (Attack Traffic) Kasada detected are thus false negatives left over by the upstream service.
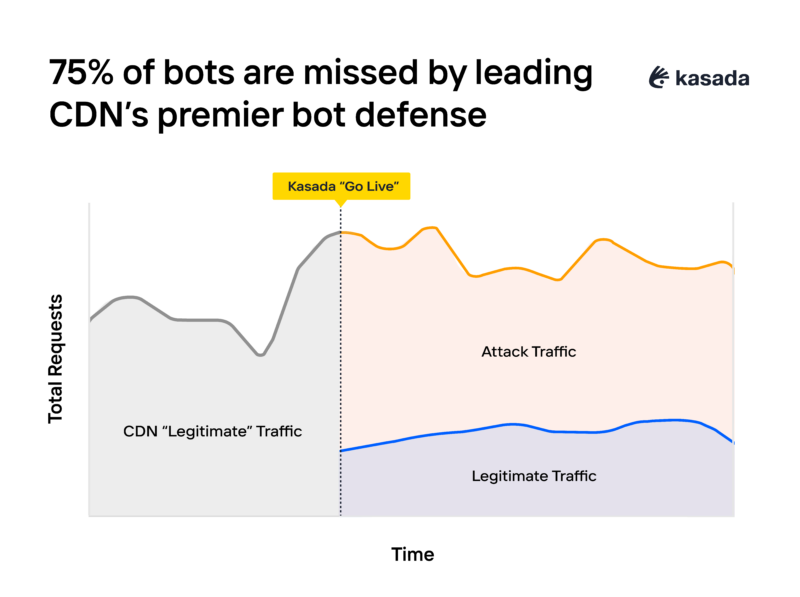
The chart above illustrates how Kasada, deployed behind the customer’s current CDN bot detection service, successfully identified and stopped bad bots that the upstream service missed. The stark contrast between the two reveals the extent of the problem — a whopping 75% of traffic the CDN lets through is actually bots. This experience is typical of customers who come to Kasada and are using a CDN-based bot management provider.
How are the botters evading the CDN’s protections? In this case, the botter is using a rotating residential proxy, making themselves appear to come from US ISPs to blend in with legitimate customer traffic. They’re also falsifying their data telemetry to appear as a Chrome browser on Windows – likely through telemetry forgery or replaying a previous legitimate challenge – allowing them to readily bypass the CDN-based bot detection service.
However, when Kasada inspects these requests, we force the telemetry collection to execute in real-time. Kasada sees this isn’t even a browser at all – it is a shell script or other non-browser because it cannot run JavaScript. Kasada stops these requests without the requirement of any configurations to update or rulesets to tweak.
How Kasada Ensures Data Authenticity
When Kasada intercepts a request, we perform two important actions (well, we do a lot more, but that’s for another day!)
- Secure the integrity of client-side data collection by forcing attackers to run their code in real-time, within Kasada’s controlled environment, which exposes their true nature. We accomplish this with our lightweight, high-performant proprietary JavaScript virtual machine that runs within the execution environment (e.g. browser, mobile app, etc.) to protect the client-side data collection from attempts to falsify the telemetry. Think of it as making a student take a test using pen and paper in a room by themselves, with a teacher observing, and no calculator or other way to cheat.
- System-wide data integrity checks secure the integrity of not only the client-side data collection process but also the transfer and collection of data from client-side to server-side to ensure no tampering has occurred in-flight.
Combining these two steps gives Kasada a high degree of confidence that the data we are acting upon is “clean” and hasn’t been tampered with. It serves as the basis for Kasada defenses to make highly accurate decisions based on a combination of client-side telemetry and machine learning (ML) based anomaly detection.
Don’t Let Attackers Into the Vault
Let’s revisit “Ocean’s 11.” The first person to enter the vault is Yen, a gifted acrobat. He evades the sensors via astoundingly difficult leaps and climbs. Why did this work? Because he had advance knowledge of the vault’s layout – and just as critically – he knew it would stay the same.
This is a pretty accurate view of how attackers bypass defenses. They “scout the layout” (figure out what signals the defenses are listening for to label as “human”) and feed that exact data, knowing the “room will stay the same” (the defenses won’t change).
Kasada avoids this problem of a static vault with faked data in these ways:
- Randomization and dynamism of defenses across Kasada’s architecture make it arduous and expensive to crack. And in the rare event of success, all their hard work is undone because the “vault” looks different next time. It’s never the same puzzle twice.
- New defense updates are made quickly. Security patches typically take days or weeks to implement – plenty of time for attackers to exploit. Kasada’s dynamic defense updates are faster, shortening the attack window and saving customers millions in financial and reputational damage.
We’ve heavily invested in a system in which every layer and nearly every aspect of the defense changes easily and quickly. This contrasts with most anti-bot systems whose defense logic and scripts aren’t well hidden and change infrequently. New updates take time to develop, and then adversaries crack them in as little as 30 minutes – creating a never-ending cycle of being too slow to keep up with adversarial retooling.
Benefits Beyond Bot Defense
The cybersecurity function can be siloed, and it’s easy to forget there’s life outside the firewall. But the impact of stopping fake bot traffic multiplies downstream: lower costs for infrastructure and SMS verification, less fraud remediation, and avoiding reputational damage that can wipe massive amounts off a market cap.
Another major benefit: Better business analytics. Our customers value their clean customer traffic data after Kasada strips out the fake and unwanted traffic. Teams across various functions leverage this data, confident that it truly represents their legitimate customers.
Questions to Ask Your Bot Protection Provider
Here are some questions you can ask your current or future bot protection vendor to assess their ability to ensure data authenticity, prevent tampering, and adapt to evolving threats.
- How do you ensure the data collected on the client-side can’t be faked?
- Can you ensure client-side data hasn’t been tampered with while processing within the system?
- If you don’t collect client-side data, how do you ensure the server-side data can’t be faked?
- Are you randomizing scripts and defense logic to ensure your protections are constantly evolving and difficult to decipher as a deterrent?
- Do you provide drill-down reporting for bad bots stopped, as well as human traffic reporting, to hold yourself accountable for false negatives?
Parting Thoughts: The Bedrock of Bot Defense
Going forward, the bedrock of bot defense must be to ensure the data collected is reliable and authentic. The most sophisticated detection and machine learning algorithms will be of limited value if the data input can’t be trusted.
To defend against modern adversaries, businesses must prioritize the authenticity of the data collected by their anti-bot providers. Those who fall short will find their customers dissatisfied with false positives, fraud, and high costs, impacting company profits, customer loyalty, and brand reputation.
Are your existing bot defenses being bypassed? Request a free KasadaIQ Snapshot, based on our collection of non-traditional data sources, to find out and help identify gaps in your current environment and shore up your bot defenses.




